Part 4 - Hubs, Switches and Routers
Although hubs, switches, and routers look very similar to each other from the outside, they perform distinct functions. They operate at different layers in the OSI Reference Model and are used for different reasons in networks.

Figure 4-1: A hub, switch, and router (note that they look very similar)
This figure taken from www.acc.umu.se/~tfytbk/ mattgrand/.
Hubs
Hubs are devices that operate at the physical layer, the first OSI layer. In other words, they consist entirely of hardware and perform no special functions and do not use software or algorithms of any kind. They are simply repeaters of physical signals.
A hub is used to link together several computers and other network devices (see Figure 4-2). Computers connected with a hub are in the same broadcast domain. For example, if the Server in the diagram wants to send a message to the Client, the Server sends the message to the hub. The hub cannot inspect the data, but only repeats it out of all of the devices to which it is connected. So, the other connected Hub, both PCs, and the Client all receive the message. It is up to each client to inspect the message and determine, based on the destination MAC address specified in the message, whether the message is intended for them. Devices connected to the hub are constantly ignoring traffic that is not intended for them. As you would expect, when the broadcast domain grows large, traffic begins to collide and network performance falls. Also, as you can see from Figure 4-1, hubs can be connected to other hubs in an "infinite" chain, but would drastically reduce network performance because any message sent to one hub would be sent to all the hubs and sent out every other cable.
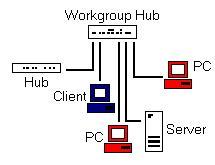
Figure 4-2: Hubs
This figure taken from www.ncifcrf.gov/communications/ networking/network_intro.htm.
An interesting note: because all devices connected to the hub receive every message sent over the network, privacy is inhibited and causes security issues arise. Most network cards can be set to "promiscuous mode" which allows the user to view all packets passing by, even if they are not intended for that computer. This can be done with hardware, such as a protocol analyzer, or with many software programs, such as "sniffers." So, if you are connected to a hub over a network, if you don't encrypt your passwords, credit cards, emails, and other sensitive information, any other user could be eavesdropping, undetected, on any information leaving or entering your computer.
A smart hub can operate above the physical layer and is able to inspect and redirect packets that pass through it. In this sense, a smart hub is not a true basic hub, but more like a switch. These days, regular hubs are rarely used in anything but a very small network.
Switches
Switches operate at the data-link layer, the second OSI layer. This layer can, among other things, inspect the packets to determine destination and source MAC addresses. Because a switch operates at this layer, it is able to direct traffic on a network. When a message enters a switch, the switch can inspect it to obtain the destination MAC address. The switch can then look up in its cache to determine which cable the message should be sent out on.
A switch builds its table dynamically. If I connect with a new device (and MAC address) to the switch, the first time I send a message that passes through the switch, the switch records my MAC address in the table next to the cable I used to connect to the switch. If the switch does not know where the destination MAC address is, it can either discard the message or send it over all the cables, waiting for a reply to record the new-found MAC address.
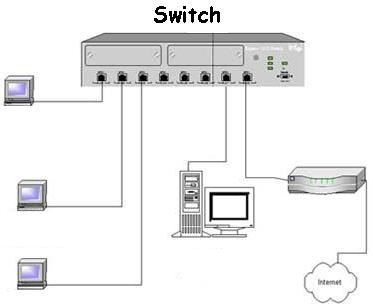
Figure 4-3: A Switch
Parts of this figure taken from support.intel.com/support/network/appliances/netstructure1500/31334.htm.
Switches increase network performance over hubs. Devices connected to switches are not in the same broadcast domain (although they can explicitly send broadcast messages). Switched networks are associated with higher network security because they are less vulnerable to packet sniffing. For these reasons, switches are strongly preferred to hubs in the corporate and large network environment.
Routers
Routers operate almost exclusively at the network layer, the third OSI layer. Routers inspect packets on the network layer and use source and destination addresses to router information. With TCP/IP, routers look at the destination IP address to determine where the packet should be sent. See the following sections for more information on routers.
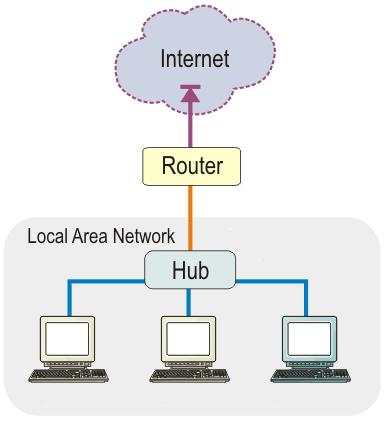
Figure 4-4: A Router connected to a network
Parts of this figure taken from www.ezmeeting.com/router.html.
Part 5 - Configuring Routers |
Back to the Index




