Part 5 - Configuring Routers
Cisco is the largest producer of routers in the world, and they carry a lot of weight in setting standards for protocols and Internet communications. I will explain how routers work in general and some specifics on Cisco routers and how to configure them. (See Figure 5-4 at the bottom of this page for a screenshot of a Cisco Router simulation program I have.)
Routers operate at the network layer of the OSI model. Routers are usually connected to several other devices, much like a hub or a switch. Routers, however, are able to direct traffic between subnets and networks.
Routers have operating systems, much like the computers we use on a daily basis. The OS interface on Cisco routers resembles the command (DOS) prompt in Microsoft or UNIX. Figure 5-1 is screenshot of a router simulation program I have, produced by Sybex. In this figure we can see part of the running configuration. We know that the router is running v 11.3 of the OS, that the password is not encrypted, the router has been named "2501A," and that there are three interfaces. We can see that two of these interfaces have been assigned IP addresses (along with subnet masks, as always).
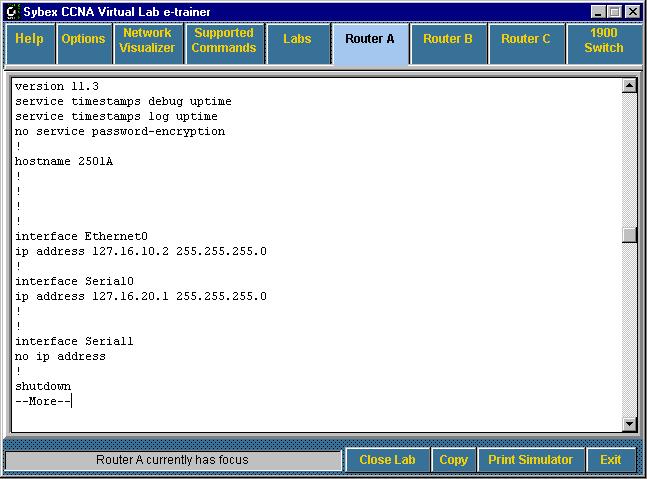
Figure 5-1: Running-Configuration of Router Simulation, General Information
Every router has two or more interfaces. Each interface is connected to a different network and must have its own IP address. The simplest kind of router is a gateway. Most networks have a single gateway that permits traffic to enter from and exit to the Internet, which has two interfaces. One interface is connected to the internal network and has an IP address belonging to that internal network. The other interface is connected to the Internet (through an ISP) and has an IP address belonging to one of the ISP's networks. The router that makes this connection is called a gateway. Computers in a network that need to communicate with other computers over the Internet must know where to look. They can configure a default gateway IP address on their machine, which would be the inside IP address of a router on the network that is connected to the Internet. This means that when the computer is unable to find a specified IP address on the local network, it sends the request to the default gateway.
A default gateway has very few choices to make. Most of its job consists of keeping internal network traffic on the inside and facilitating communication with the Internet (See Figure 4-4 for an example of a gateway router). Most routers have multiple interfaces and are assigned the task of deciding which network should be sent the packets. Routers in smaller networks usually only have one way that each packet can be sent in order to reach its final destination. In this case, the interface the packet is sent out of is dependent only on the destination IP address.
Routers in larger networks and on the Internet (such as those owned by ISPs) make more complicated decisions. They often have multiple paths that can be taken to send the packet to the destination. In this case, the criteria often include the congestion of particular routes, the average time over a particular route, the number of hops (the number of routers the packet must pass through before arriving at its destination), and the monetary cost of certain paths. Thresholds can be configured on the router to allow, for example, packets to be sent down a more expensive path only when the other paths become congested.
Routers can be configured to forward or deny certain types of traffic. This function is generally considered the responsibility of a firewall. Firewalls are specifically designed to increase security and allow for complicated rules. Many of these criteria can also be used on routers, including: protocol type, source address, destination address, port number, etc. These criteria or rules are places in access lists. An access list can have only one or two rules, or it can have hundreds. Access lists are then applied to particular interfaces.
For example, we could decide that we want to only allow traffic to be sent to a web server (IP 10.0.10.1 255.255.0.0) if it is valid web traffic, or HTTP, which is port 80 in TCP. We also want to make sure that only computers on network 20 can access this web server, and everything else should be blocked. In this case, we would need to enter commands similar to the ones shown in Figure 5-2.
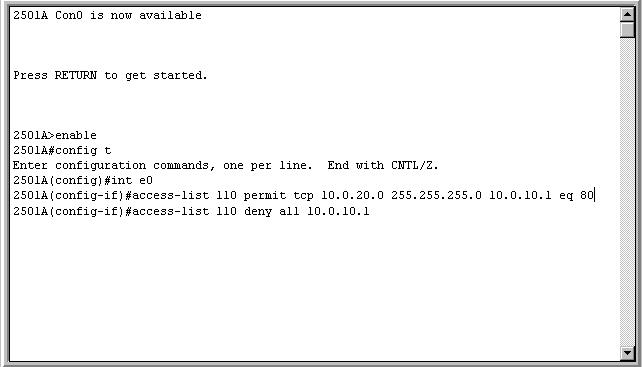
Figure 5-2: Setting up an Access-List
Here are the steps required to do so, as I have done in Figure 5-2 (we are assuming that IP addresses have already been set for the interfaces and that they are open): (1) Hit RETURN; (2) type "enable" to enable modifications to the router; (3) type "config t" to configure the interfaces; (4) type "int e0" to select interface Ethernet #0; (5) type in the code for the access list: "access-list 110" to specify the access-list number, "permit tcp" to state that this is a permission-granting line on the TCP protocol, "10.0.20.0 255.255.0.0" to indicate the 20 network, "10.0.10.1" to indicate the web server, "eq 80" to specify port 80, which is HTTP; (6) deny all other traffic to the web server. We would then apply the access-list to the interface.
Access-lists are compared to packets, one at a time, until a rule has been met. So, if we got a valid packet that we wanted to let through, then the first line (rule) would be met, and the packet would be sent through. If the packet didn't meet the criteria of the first line, it would be sent to the second and so forth (in this case it would be denied at the second line).
Routers can be configured with hundreds and even thousands of different commands. It generally takes a network engineer five to ten years to become familiar with most of these commands.
Routers can also be used to translate traffic between two different types of networks. For example, IPX/SPX can be sent over a TCP/IP network when the router modifies the packets. Routers also can transmit traffic over different kinds of physical mediums. Often a router connected at an ISP will have an interface onto a fiber optic line for increased speed.
Routers also use routing tables to decide where traffic should be sent. An example of a routing table I manually entered can be seen in the running configuration in Figure 5-3. It shows that packets destined for networks 50, 40, and 30 should be sent to 172.16.20.2.
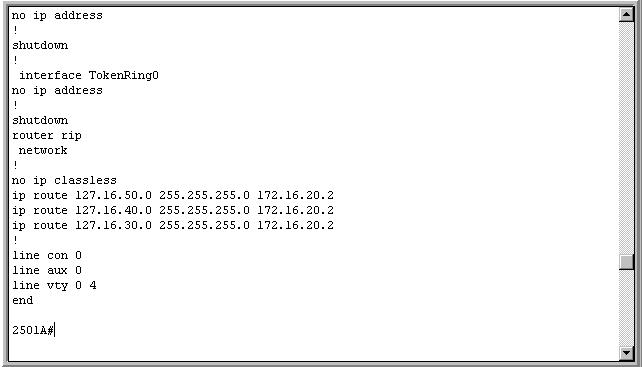
Figure 5-3: Routing Table in Running-Configuration
Routers can also be configured with a gateway of last resort, in the same way client computers can be set up with a default gateway. This gateway should almost always be set up because the router does not know where every network in the world is. When the router receives a packet destined for an unknown network, the packet is sent to the gateway (one of its neighbor routers, which is often a higher level up on the ISP or closer to the Internet backbone).
Protocols also exist to help dynamically set the routes on routers. This can help redirect traffic in real time in the case of congestion or a broken line. RIP (Routing Information Protocol) and OSPF (Open Shortest Path First) are two examples of routing protocols frequently used. (Figure 5-3 shows that I have RIP configured for the router.) These dynamic routing protocols allow routers to communicate with their neighbors to discover routes and share information in their routing tables. Some of the procedures are very complicated. The routers can be configured to send their routing tables at certain timed intervals, such as every sixty seconds.
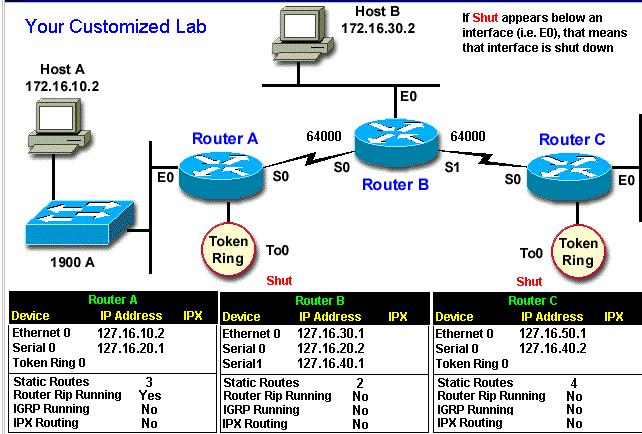
Figure 5-4: The Customized Lab I set up in the Router Simulation
Part 6 - More Information About Routers |
Back to the Index




